In a rapidly evolving cybersecurity landscape, new attack vectors are emerging at an alarming rate. One of the latest trends involves threat actors leveraging stolen credentials to distribute malicious fake browser updates through infected websites. Known as the ClickFix campaign, these attacks have targeted thousands of websites globally, using fake WordPress plugins to inject malicious scripts that lead unsuspecting users to download harmful software. This article delves into the mechanics of this attack, its impact, and how cybersecurity professionals can safeguard against such threats.
The ClickFix Campaign: An Overview
The ClickFix malware campaign first came to light in August 2023, identified by GoDaddy’s security researchers. In a new twist to classic social engineering, attackers use stolen WordPress admin credentials to install fake plugins on compromised websites. These seemingly legitimate plugins are equipped with malicious JavaScript code, which triggers fake browser update prompts on end-users’ screens. Users who fall for the fake updates end up installing malware, ranging from information stealers like Vidar Stealer to remote access trojans (RATs).
A notable aspect of these attacks is the use of blockchain technology and smart contracts. The malicious payloads are distributed via EtherHiding—a method of embedding code within Ethereum transactions, making detection even more difficult. Since its discovery, the ClickFix malware has been detected on over 6,000 sites globally, according to SiteCheck’s remote website scanner, with the numbers rising as the campaign continues.
Fake WordPress plugins
“The fake plugins use generic names such as “Advanced User Manager” or “Quick Cache Cleaner”. Their directories contain only 3 small files:
wp-content/plugins/quick-cache-cleaner/ -rw-r--r-- 1 [redacted] [redacted] 6148 Sep 2 01:15 .DS_Store -rw-r--r-- 1 [redacted] [redacted] 829 Sep 2 01:15 index.php -rw-r--r-- 1 [redacted] [redacted] 2255 Sep 2 01:15 qcc-script.js
wp-content/plugins/advanced-user-manager/ -rw-r--r-- 1 [redacted] [redacted] 2255 Sep 3 00:57 aum-script.js -rw-r--r-- 1 [redacted] [redacted] 833 Sep 3 00:57 index.php -rw-r--r-- 1 [redacted] [redacted] 6148 Sep 3 00:57 .DS_Store
Researchers quickly noticed the JavaScript file naming pattern consisting of the first letter of each word in the plugin name, appended with “-script.js”. For example, the “Advanced User Manager” plugin contains the aum-script.js file.
This naming convention allowed our researchers to detect several malicious plugins, including the Easy Themes Manager, Content Blocker, Custom CSS Injector, etc. In some cases, the malicious JavaScript file is simply named script.js:
| Plugin name | Injected script |
| Admin Bar Customizer | admin-bar-customizer/abc-script.js |
| Advanced User Manager | advanced-user-manager/aum-script.js |
| Advanced Widget Manage | advanced-widget-manage/awm-script.js |
| Content Blocker | content-blocker/cb-script.js |
| Custom CSS Injector | custom-css-injector/cci-script.js |
| Custom Footer Generator | custom-footer-generator/cfg-script.js |
| Custom Login Styler | custom-login-styler/cls-script.js |
| Dynamic Sidebar Manager | dynamic-sidebar-manager/dsm-script.js |
| Easy Themes Manager | easy-themes-manager/script.js |
| Form Builder Pro | form-builder-pro/fbp-script.js |
| Quick Cache Cleaner | quick-cache-cleaner/qcc-script.js |
| Responsive Menu Builder | responsive-menu-builder/rmb-script.js |
| SEO Optimizer Pro | seo-optimizer-pro/sop-script.js |
| Simple Post Enhancer | simple-post-enhancer/spe-script.js |
| Social Media Integrator | social-media-integrator/smi-script.js |
Most of these malicious fake plugins have over five hundred detections on PublicWWW at the time of writing. Based on the analysis done by GoDaddy Security, we estimate over 6,000 unique domains worldwide have been impacted by this recent variant.
Plugin code
The contents of the fake plugins are pretty simple. You can view the entire PHP code (including comments) on one screen.
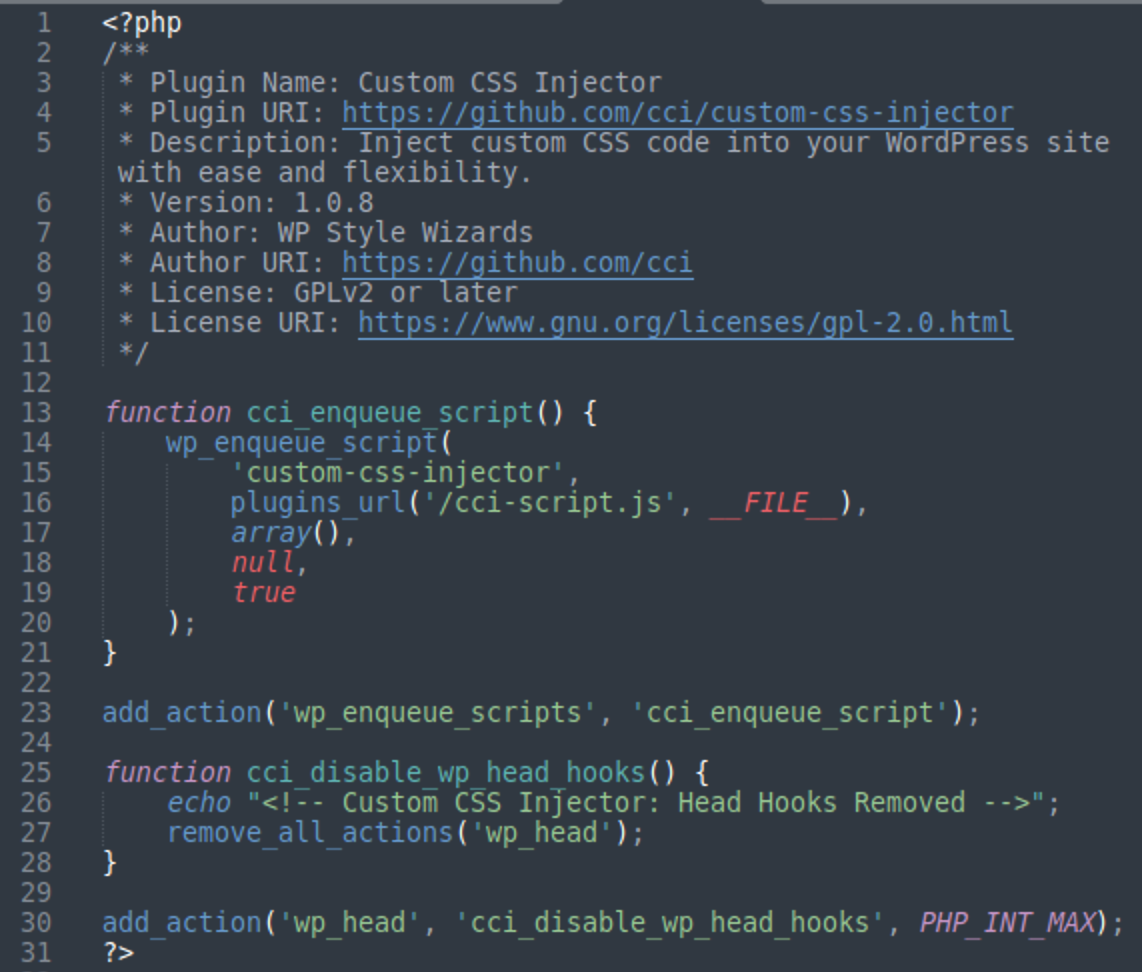
All information in the plugin metadata is fake (the Plugin Name, URL, Description, Version, Author, Author URI, etc) but it looks pretty plausible at first glance. ” GoDaddy.
How ClickFix Works
Threat actors initiate their attacks by infiltrating WordPress sites using stolen credentials. Once inside, they install fake plugins with generic names like “Advanced User Manager” or “Quick Cache Cleaner.” These plugins contain minimal code, designed to avoid detection. The main threat, however, lies within JavaScript files like qcc-script.js and aum-script.js, which are embedded in WordPress pages. These scripts display fake browser update prompts to website visitors, often mimicking legitimate updates for popular browsers like Chrome or Firefox.
The malicious JavaScript code is designed to download malware onto the victim’s device. The code interacts with blockchain smart contracts, using them to fetch the payload. Once executed, the malware can allow attackers to gain control over the infected system, steal sensitive information, or even further propagate the attack to other users.
The Scale of the Attack
By June 2024, over 6,000 websites were confirmed to have been compromised by the latest ClickFix variant, according to GoDaddy’s security reports. These compromised websites span multiple industries and countries, affecting unsuspecting visitors who trust the legitimacy of the sites they visit. The fake plugins have also been identified by public databases like PublicWWW, with over 500 detections per plugin, further highlighting the widespread nature of this threat.
In many cases, attackers were found using auto-generated fake plugins that mimicked legitimate ones, such as “LiteSpeed Cache Classic” or “SEO Booster Pro.” These plugins contained a single index.php file designed to inject the ClickFix JavaScript into web pages. Once the malicious script is in place, the malware can continue its work without drawing attention, making it difficult for website owners to detect and remove the threat.
10 Key Strategies to Prevent ClickFix Attacks
With the ClickFix malware spreading rapidly, it’s crucial for website administrators and cybersecurity professionals to take proactive steps to protect their systems. Here are 10 essential strategies to prevent similar threats in the future:
- Enable Multi-Factor Authentication (MFA): Protect your WordPress admin accounts with MFA to prevent unauthorized access, even if credentials are stolen.
- Regularly Audit Plugins: Regularly check all installed plugins and remove any that are outdated, unused, or from unverified sources.
- Use Security Plugins: Install reputable security plugins that can monitor file integrity and detect malicious code injections in real-time.
- Enforce Strong Password Policies: Ensure that all admin accounts use strong, unique passwords and enforce regular password changes.
- Limit Login Attempts: Configure WordPress to limit login attempts and block IP addresses after multiple failed attempts, reducing the risk of brute force attacks.
- Monitor Website Traffic and Logs: Use tools to monitor web traffic and server logs for unusual activity that could indicate a breach.
- Update WordPress and Plugins Regularly: Keep your WordPress installation and plugins updated to the latest versions to protect against known vulnerabilities.
- Backup Website Data Frequently: Regular backups will ensure that you can quickly restore your website in the event of a compromise.
- Use a Web Application Firewall (WAF): A WAF can help block malicious traffic before it reaches your website, acting as a first line of defense.
- Conduct Regular Security Audits: Periodically review your website’s security posture with professional audits to identify and fix any weaknesses.
Conclusion
The ClickFix malware campaign is a prime example of how cybercriminals are evolving their tactics, leveraging sophisticated techniques like blockchain to conceal malicious activity. By using fake browser updates as a social engineering tool, attackers can easily trick users into downloading harmful software. For website administrators, the importance of securing credentials, auditing plugins, and implementing multi-layered defenses cannot be overstated. As the cybersecurity landscape continues to shift, staying vigilant and employing best practices is the key to safeguarding against threats like ClickFix.
Source: GoDaddy
Want to stay on top of cybersecurity news? Follow us on Facebook – X (Twitter) – Instagram – LinkedIn – for the latest threats, insights, and updates!




