On 22 May 2025, cybersecurity sources confirmed a major data breach targeting Coca-Cola Company’s Middle East operations. Claimed by the Everest ransomware group, the leak has exposed highly sensitive employee data including government ID scans and internal administrative documentation on both the dark web leak site and a Russian-language cybercrime forum. This breach raises urgent concerns across global and regional cybersecurity communities due to the depth of leaked data and the potential for long-tail exploitation through phishing, impersonation, and fraud.
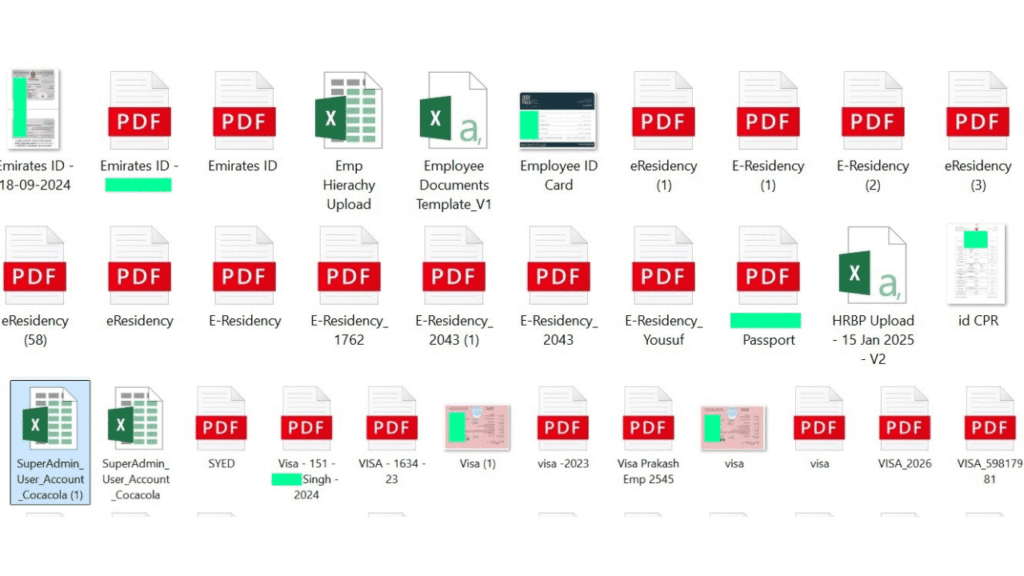
On 22 May 2025, Hackread.com reported that Everest ransomware had leaked a 502 MB archive containing Middle East-specific internal records and employee data from Coca-Cola. The dump includes passports, visas, family documents, HR mappings, and administrative structures of Coca-Cola staff based in the UAE, Oman, and Bahrain.
This isn’t just a corporate breach; it’s a human security incident that may impact employees’ personal safety and national-level privacy regulations, especially in jurisdictions like the UAE where data protection is tightly governed.
Timeline of Verified Events
22 May 2025 – Breach Disclosure
- Hackread.com confirmed Everest’s leak.
- 1,104 files, totaling 502 MB, were posted publicly.
- Data was published on Everest’s leak portal and the XSS underground forum.
Key Files in the Leak
- SuperAdmin_User_Account_Cocacola: Reveals admin account roles and privileges.
- Emp Hierarchy Upload: Details job titles, manager structures, and reporting chains.
- HRBP Upload: Shows departmental HR assignments and user ID mappings.
Coca-Cola’s Response
As of 28 May 2025, Coca-Cola has not released a formal statement. It remains unknown whether:
- Ransom demands were made,
- Any negotiations occurred,
- Authorities or regulators have been officially engaged.
Middle East and Africa Perspective
The leak affects Coca-Cola staff in UAE, Oman, and Bahrain, raising potential GDPR-equivalent violations under:
- UAE Federal Law No. 45 of 2021 on Personal Data Protection,
- Oman’s Cybercrime Law, and
- Bahrain’s Personal Data Protection Law (PDPL).
Organizations operating in the MEA region must now re-evaluate supply chain cybersecurity, especially when handling personal data across borders. Failure to notify impacted users or regulators could result in heavy fines and reputational damage.
Global Context: Not an Isolated Incident
The Coca-Cola leak adds to an escalating pattern of ransomware groups targeting corporate backbones via employee data and admin-level configurations. Similar tactics were recently used by:
- Silent Ransom Group, flagged by the FBI in April 2025,
- LockBit, in its campaign against a European logistics firm,
- BlackCat (ALPHV), which breached sensitive educational data in Australia.
These attacks increasingly bypass perimeter defenses, focusing instead on mapping internal structures and conducting highly targeted social engineering campaigns.
Expert Perspectives
“This leak isn’t just a breach of corporate security—it’s a blueprint for further attacks. The HR mappings and admin roles are goldmines for threat actors,”
— Ali Khan, Director of Threat Intelligence, Kaspersky MEA, in a CyberCory.com interview, 27 May 2025.
“With this level of leaked personal documentation, we’re talking identity theft, SIM-jacking, and nation-level surveillance risks.”
— Dr. Rasha Al-Salem, Cyber Risk Analyst, Gulf Cybersecurity Forum, 28 May 2025.
MITRE ATT&CK Techniques, TTPs & IOCs
🛠️ TTPs Used:
- T1078: Valid Accounts – mapping privileged accounts
- T1589: Gather Victim Identity Information
- T1566: Phishing (potential for post-leak exploitation)
- T1598: Spearphishing Link
- T1083: File and Directory Discovery
📎 IOCs (from Everest leak):
- Filename: SuperAdmin_User_Account_Cocacola.xlsx
- Filename: HRBP_Upload.xlsx
- Domains: [Redacted for safety]
- Forum: xss.is (Everest ransomware publication point)
Actionable Takeaways for Security Leaders
- Audit access to HR systems and internal admin panels regularly.
- Apply the principle of least privilege—limit who can see employee personal data.
- Implement Zero Trust Architecture for segmented access and internal privilege control.
- Scrub leaked user IDs and emails against current systems—revoke or rotate access.
- Launch phishing simulations targeted at employees in high-risk departments.
- Encrypt sensitive internal records at rest and during transit.
- Coordinate with regulators in MEA countries to ensure compliance and avoid fines.
- Develop incident communication plans specifically for data leaks impacting staff.
- Patch legacy systems to minimize vulnerabilities in HR or document management tools.
- Engage third-party forensic teams for deep leak analysis and future breach prevention.
Conclusion
The Everest ransomware breach of Coca-Cola’s Middle East employee data represents a dangerous evolution in cybercrime where attackers aim not just for ransom payments, but to weaponize internal corporate intel for future attacks. With no public statement yet from Coca-Cola, the breach raises alarm bells across industries, regulators, and employee privacy advocates. Organizations must now prioritize insider mapping protections and assume internal exposure is inevitable unless defenses shift from perimeter security to human-centric risk models.
Sources
- Hackread.com – Everest Leaks Coca-Cola Employee Data (22 May 2025)
- CyberCory.com – Cybersecurity News, Updates & Best Practices
- IC3 FBI PSA – Ransomware Trends (April 2025)
- SaintyNet – Cybersecurity Services & Awareness
- UAE Personal Data Protection Law – Official PDF
- Bahrain PDPL – Official Portal
- MITRE ATT&CK Enterprise Matrix




