Daniel Ehrenreich, BSc. is a consultant and lecturer acting at Secure Communications and Control Experts (SCCE) and periodically teaches and presents at industry conferences on the integration of cyber defense with industrial control systems; Daniel has over 33 years of engineering experience with ICS and OT systems for electricity, water, gas, and power plants as part of his activities at Tadiran, Motorola, Siemens, and Waterfall Security. Re-selected as Chairperson for the 9th ICS-OT-IIoT CyberSec 2025 event in Israel on 8-1-2025

What are the most critical concerns about the assurance of safe and reliable operation of cyber-physical systems such as critical utilities, manufacturing, process industries, etc?
Introduction
In recent years, industry experts were periodically informed on many new vulnerabilities related to Programmable Logic Controllers (PLC), Remote Terminal Units (RTU), Human Machine Interface (HMI) and Intelligent Electronic Devices (IED), supplied by a range of well-known vendors. These exposures lead to growing concerns among systems’ operators about possible cyber-attacks against Industrial Control Systems (ICS) / Operation technology (OT) systems. However, the published incidents worldwide contradict those publications, and the number of attacks impacting the ICS-OT operation was low. Among the published internally and externally generated cyber security incidents, you find attacks that may directly or indirectly affect the industrial process and cause operation outages, damage to machinery, and risks to lives.
What are the most important actions every organization must conduct to ensure business operation continuity, risk reduction, and minimize damages when an incident occurs?
To protect the business operation continuity of your plants, you must be more concerned about the incidents caused by failures, uncorrected actions by authorized personnel, and internal or external or supply chain-initiated cyber-attacks. This paper aims to help readers understand IT and OT-related cyber incidents and select suitable and cost-effective cyber defense solutions that ensure the facility’s operating safety, reliability, and availability (SRA).

Incident analysis
The following paragraphs will guide you through multiple scenarios that describe the popular ICS-OT-related cybersecurity incidents and explain why they might occur.
- How do cyber incidents happen?
Here, we must differentiate between failures created by a) OT products or software bugs, b) incorrect actions by authorized personnel, and c) cyber-attacks, which can be internally, externally- generated, or supply-chain initiated. Upon analyzing the details in Figure 1, your organization may select the most suitable risk mitigation solution to minimize the impact caused by an incident.

- Which factors might lead to a cyber-attack?
According to Figure 2, cybersecurity incidents are typically initiated following three factors. a) the ICS-OT architecture might have one or more unsolved vulnerabilities caused by hardware, software, physical security, or poorly structured program; b) someone might have a or strong motivation; and c) the attacker has the confidence that the planned attack is possible and can be completed successfully.


- Factors allowing the cyber incident
When analyzing the contributing factors causing the incident, Figure 3 points to the following: a) poor physical/ perimeter protection, b) insecure design of the ICS-OT program, and c) lack of attention to factors described by the PPT (People-Processes-Technologies). Furthermore, organizations must ensure that physical processes are conducted and controlled according to “Security by Design” principles.

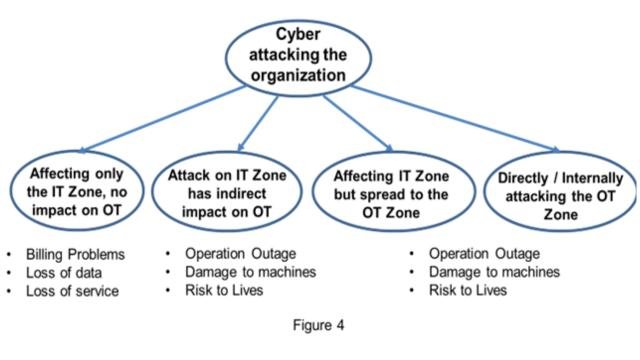
- Consequences of a cyber-attack against IT and OT Zones in an organization
When analyzing the possible impact on an industrial facility, as shown in Figure 4, it is essential to pay attention to a) Incidents impacting only the IT Zone, b) Incidents against the IT Zone that might indirectly affect the OT Zone, c) Incidents against the IT Zone but the attack might proceed to the OT Zone and finally incidents aiming to impact the OT Zone and cause operation outage, damage or risk lives.
Summary and Conclusions
ICS-OT cyber security experts know well that to select the most suitable, effective, and cost-effective cyber defense, their team must understand the plant’s control process. Once these studies are completed, the local teams can analyze the sources of malfunctioning cyber-attacks, evaluate who or which organizations might initiate the attack. Experts must accurately analyze the possible attack vectors (using the practical tools mentioned above) and assess the possibility of conducting a direct attack on the ICS-OT zone or an attack that might start by compromising the IT architecture and the segregating barriers.
Consequently, it is essential to strengthen the notion that solid perimeter/physical defense is a mandatory precondition to cyber security, and robust cyber security and network segregation are mandatory preconditions to operating safety. Finally, IT and ICS-OT experts must collaborate to select and deploy correctly designed cyber defenses. The role of the management at industrial and utility-related facilities is to allocate the needed resources to be at least one step ahead of hostile attackers.




